I have heard about Windows Defender Application Guard (WDAG) for quite sometime but have not had the chance to investigate further. I came across some articles on it while doing research on container networking and decided to try it out on my own and to document my experience here.
In a nutshell, WDAG is a Windows Feature that allows you to isolate your browsing session in the Edge browser to protect against attack from malicious websites. This is achieved by using Hyper-V technology but do not require you to start/create/manage a VM. The isolated Edge browsing session is automatically started, like a new application. It also consumes less resources compared to a full fledged VM. It was first made available in version 1709, but it requires Windows 10 Enterprise version. Starting with version 1803, it can be enabled in Windows 10 Professional too.
Enabling Windows Defender Application Guard
Ensure that you have Windows 10 Professional 1803 and above. There are also some additional prerequisites that you can check out here.
Click Start and type/paste ” Turn Windows features on or off “, click on the search result.
From the dialog box, select “Windows Defender Application Guard”
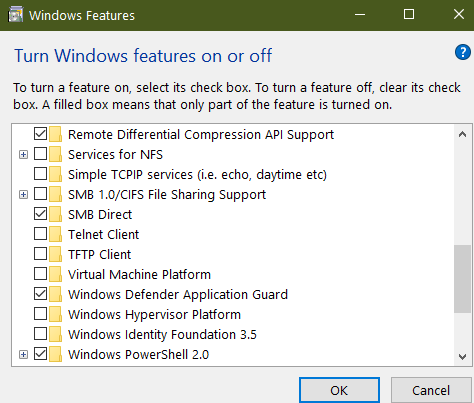
Or you can simply type the command below on an elevated Powershell
Enable-WindowsOptionalFeature -online -FeatureName Windows-Defender-ApplicationGuard
Restart when prompted.
Using Windows Defender Application Guard
Once installed, it is super simple to use. Just launch the edge browser and click on the … on the top right hand side. You should see a “New Application Guard Window” option.
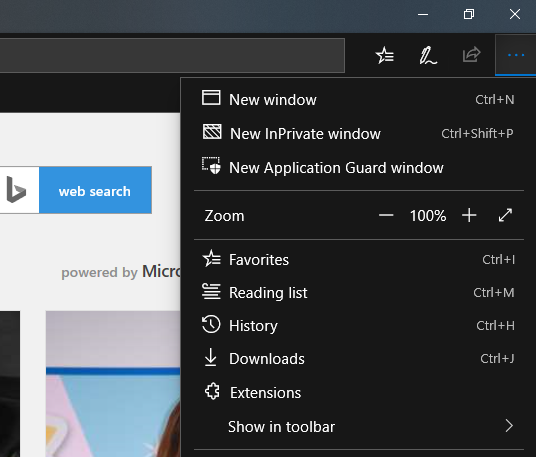
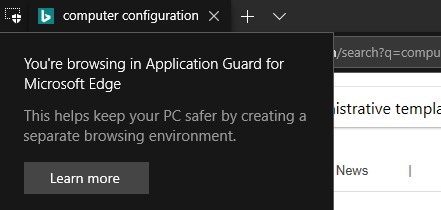
It might be hard for you to identify the WDAG isolated version of Edge. But if you look at the top left hand corner, you can see an icon and clicking on it will display a message that lets you know you are using WDAG version of Edge.
To test the isolation, simply go to any websites and try downloading a file. You will be able to save the file, but only in its own isolated application guard folder. You will not be able to copy/paste/drag and drop the file to your desktop. Also noticed the different icon for the WDAG version of Edge. Also by default, the data is non persistent. All data will be deleted if after you logoff from your Windows.
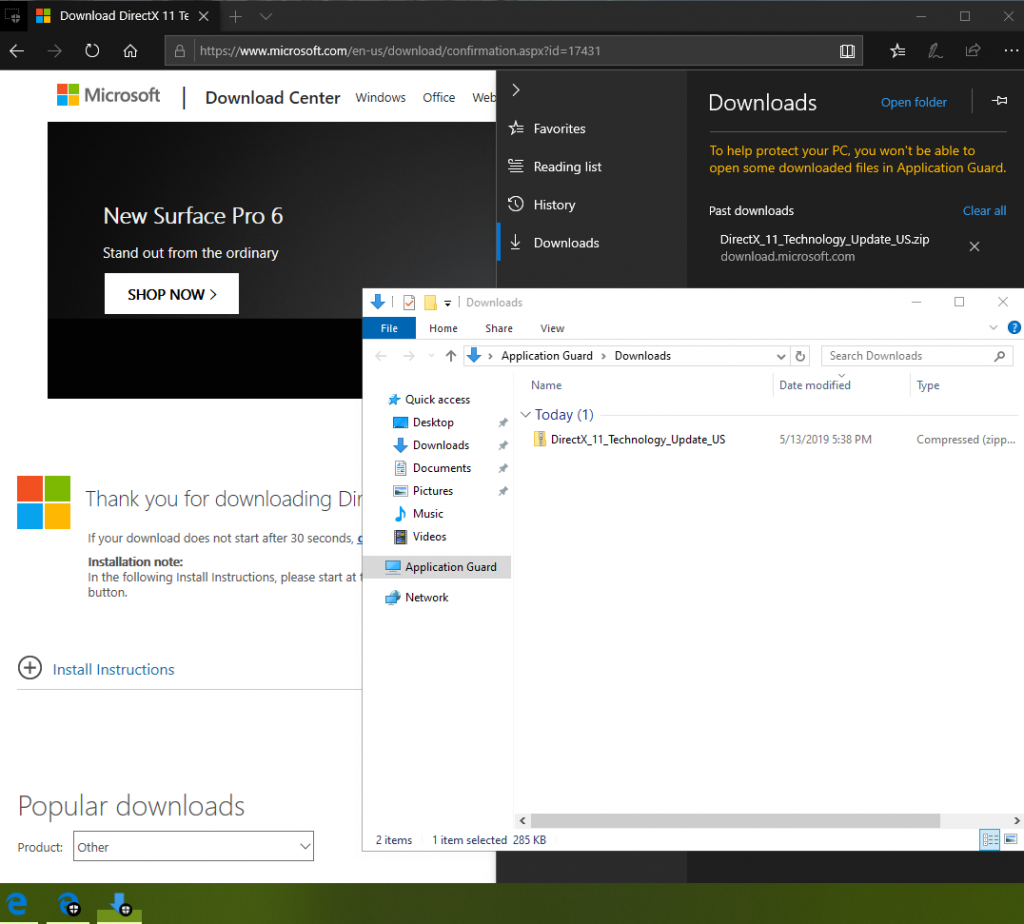
Note the Application Guard PC name
Usage Scenarios
As an individual, you can use this when you need to visit some shady websites, such as those that comes with lots of pop ups and advert. You can have some assurance that any malicious content will be isolated.
For Enterprise usage, the administrator has various policies that they can configure, such as controlling clipboard access from the host, the ability to print and whether to persist the “isolated image” in between launches using Group Policy Objects. You will also have the option to manage these policies through more “modern” options such as System Center Configuration Manager or Microsoft Intune.
Some interesting observations
I am pretty sure that the WDAG session is running in a Hyper-V VM but you will not see it in your Hyper-V manager.
You will find a virtual Hyper-V network adapter call “vEthernet (Hvsilcs)”, but it is not associated with any Hyper-V virtual switch. I guess this is the “hidden” network that pass network traffic to the isolated browser session.
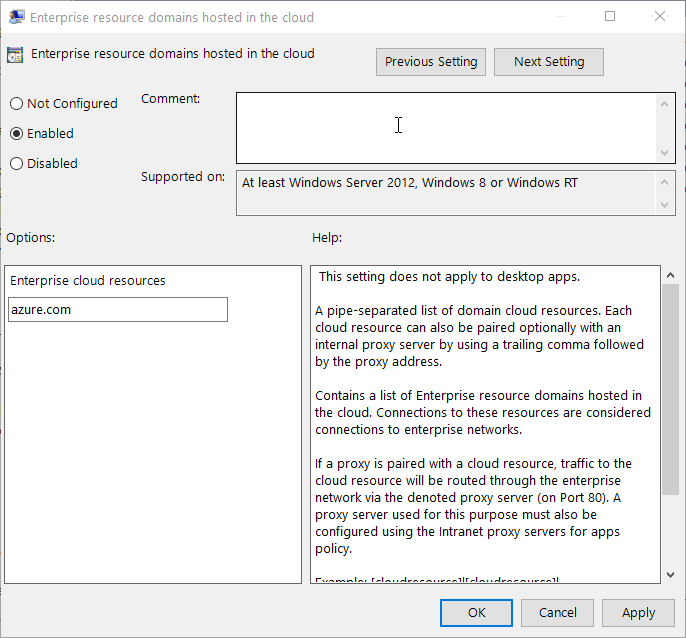
There are a couple of interesting WDAG related GPO.
Administrative Templates\Network\Network Isolation\Enterprise resource domains hosted in the cloud. This allow you to configure a comma separated list of domain names that are allowed to be used in the normal Edge browser. If you attempt to open a page in other domain outside of this, a page will be displayed indicating that you have to open it in WDAG.
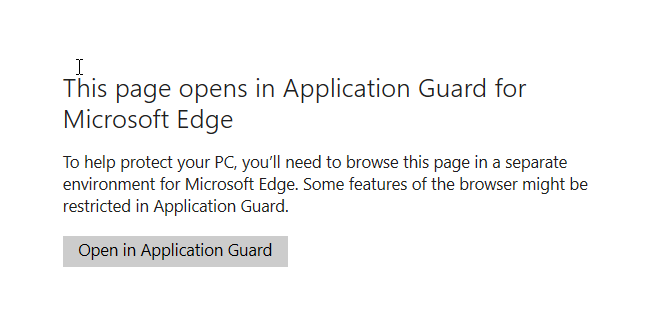
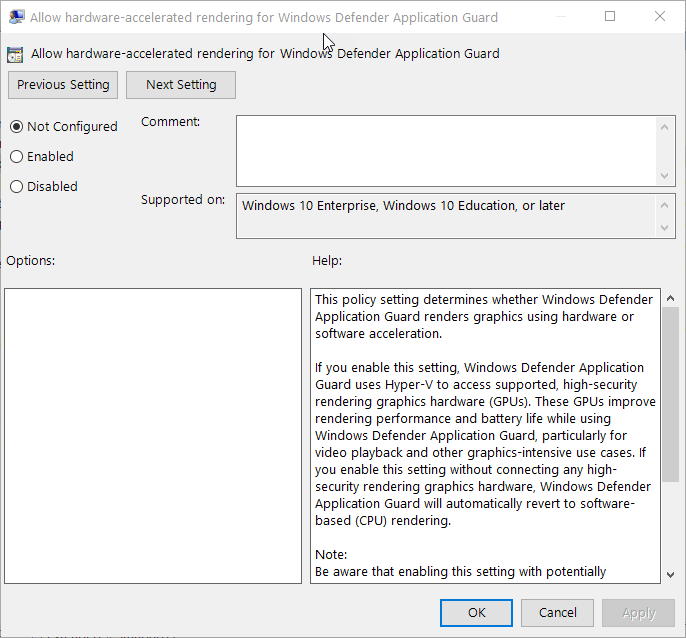
I also find performance noticeably slower, especially on page with video content. This is because the WDAG version of Edge is only using software rendering. To use GPU hardware based acceleration, you will have to configure this setting
Computer Configuration\Administrative Templates\Windows Components\Windows Defender Application Guard\ Allow hardware-accelerated rendering for Windows Defender Application Guard
Another interesting setting is the clipboard control available in this GPO setting :
Computer Configuration\Administrative Templates\Windows Components\Windows Defender Application Guard\Configure Windows Defender Application Guard clipboard settings
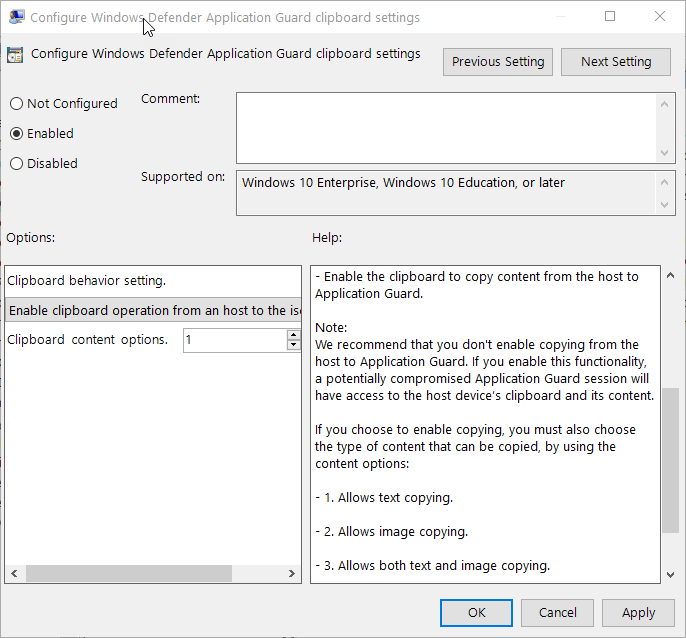
The options includes :
- Block
- Copy and paste from the isolated session to the host PC
- Copy and paste from the host PC to the isolated session
- Copy and paste both directions
The ability to “Firewall” clipboard direction is cool!!
You can also choose what to allow:
- Option 1 Allow Text only.
- Option 2 Allow images only.
- Option 3 Both Text and images
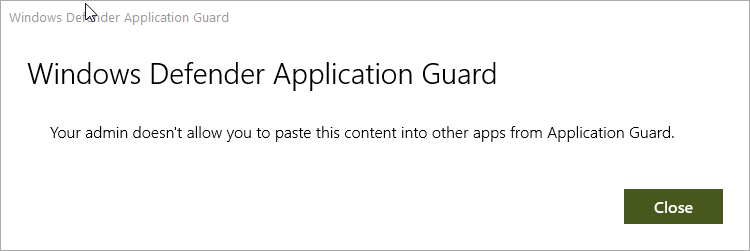
If you attempt to violate the copy rule, you are greeted with a message like the one below
What about Edge Chromium?
You might be glad to know the Microsoft has recently extended this to the Chromium version of the Edge that they have been busy developing.
Simply install the latest version of Dev channel available here. After you have enabled WDAG as detailed above, simple launch Edge Chromium and type in edge://flags in the address bar. Search for guard and you should see the option. Enabled the option and relaunch Edge Chromium.
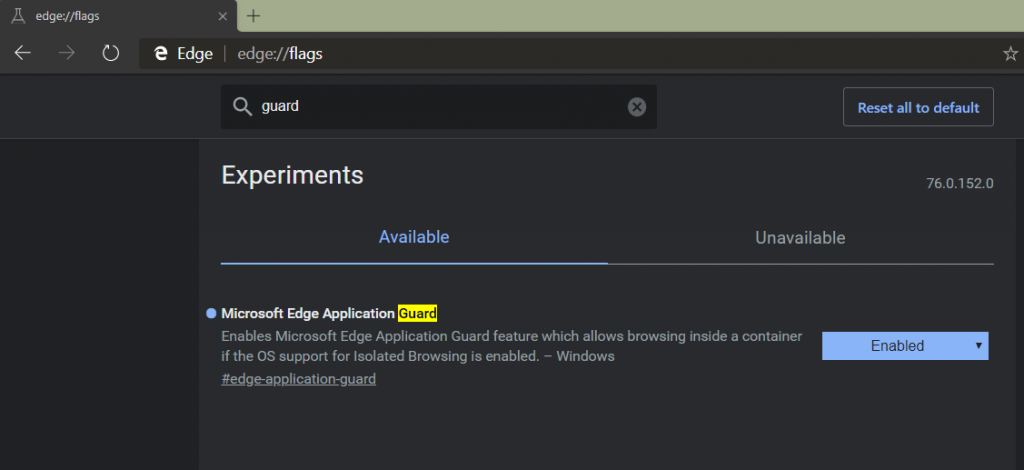
You will now get the same “New Application Guard Window” option when you click on the … in the top right corner of an Edge Chromium window.
I have been using Edge Chromium Dev channel for quite sometime now and it is stable enough for me as a default browser. The ability to use WDAG with it is reason enough for you to try it if you haven’t done so.
Hope this is useful to you. Stay secure and browse safely.
Cheers
CY
